CS 417 Exam 2
Spring 2006
- 5 points
Why is Coda not well suited to hosting a shared database? - 6 points
When does an AFS client get an updated copy of a file that was modified on another system? - 6 points
CIFS supports a SEEK command, which sets the current read/write position in the file. NFS does not have this. Is this a deficiency in NFS? Explain. - 6 points
What is false deadlock? - 5 points
What is false sharing? - 6 points
Assign Lamport timestamps to the following events: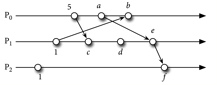
a. d. b. e. c. f. - 6 points
You have a several computers cooperating on a parallel program. CPU 1 tries to write to page 302, which is currently owned by CPU 0. Explain the sequence of operations that takes place.Part II - 60 Points
For each statement, select the most appropriate answer.
- Which of the following is not a valid NFS v3 RPC:
ACCESS: check access permissions.
CLOSE: close a file.
MKNOD: create a special device file.
GETATTR: get file attributes. - Oplocks are designed to:
control server-side caching.
control client-side caching.
allow clients to perform advisory file locking.
ensure that only one client accesses a file at a time. - The NFS automounter was not designed to:
provide a way to offer the same namespace to a set of systems.
provide a way to mount all remote resources when the system boots up.
mount remote resources on demand.
minimize the number of actively mounted remote resources on a system. - Which of the following is not a condition for deadlock?
Hold & wait: processes that hold resources can wait for another one.
Non-agreement: two or more processes cannot agree on resource allocation.
Non-preemption: a resource cannot be revoked from a process that has it.
Circular wait: two or more processes are waiting for resources held by one of the others. - Which set of events is concurrent (all events are concurrent with each other)?
(3, 1, 5, 7), (3, 2, 6, 7), (2, 1, 6, 8)
(2, 1, 3, 4), (2, 2, 3, 3), (3, 3, 2, 5)
(1, 2, 3, 4), (2, 3, 4, 5), (3, 4, 5, 6)
(1, 5, 6, 7), (1, 4, 5, 7), (1, 3, 2, 2) - After the first phase of a two-phase commit protocol, the coordinator:
sent out a query asking whether the cohorts are ready to commit.
received responses to the query from all cohorts.
sent a request to commit (or abort) but did not receive acknowledgements.
received acknowledgements to the commit (or abort) directive. - A linear compensating function adjusts a clock to:
tick at constantly decreasing or increasing intervals until synchronization is achieved.
compensate for variations in a clock's frequency to make it appear to tick at a constant rate.
tick at a constant faster or slower interval.
compensate for sudden changes such as leap seconds and daylight saving time. - A client gets a timestamp of 4:12:30.500 from a time server. The elapsed time between the request and response was 20 msec (0.020 sec). The current time on the client is 4:12:30.510. Using Cristian’s algorithm, what is the time set to on the client?
4:12:30.480
4:12:30.490
4:12:30.510
4:12:30.520 - Which mutual exclusion algorithm is useful when the membership of the group is unknown?
Centralized.
Lamport's.
Token ring.
All of these algorithms require knowledge of all group members. - How does IP multicast achieve reliable packet delivery?
It doesn't.
Via best-effort multicast.
Via atomic multicast.
Via IGMP (Internet Group Management Protocol). - A copyset is used:
in a DSM system that employs page caching.
in a DSM system as an alternative to page caching.
to implement lazy release consistency.
to implement entry consistency. - Weak consistency models do not allow:
read-write operations to the same memory location to be reordered.
read-write operations to different memory locations to be reordered
delayed writes to cached copies of pages.
cached copies of shared memory pages.